iCloud, iHack, iSpam – iCloud SMS Spam Explained
While on a trip to New York City you might find yourself walking down 5th Avenue peering into the windows of designer stores such Coach, Prada, Louis Vuitton, and Gucci to view mannequins wearing the latest clothing, sunglasses and of course – the latest handbag. The purse in the store probably costs more than your plane ticket to NYC, so you opt to pick up a less expensive counterfeit one from a stand around the corner for around $100. You know it’s fake, but you also know that from afar, most can’t tell the difference. The purveyors of these counterfeit luxury goods have the billion-dollar market cornered, and from what we can tell, they are trying to expand their aggressive advertising methods into that rising star of consumer markets: China. In doing so, they have uncovered a significant new method exploiting the way that the Apple iPhone operates with other devices.
The Attack
While Enea AdaptiveMobile Security deals in multiple types of SMS abuse like account phishing and loan scams, one ongoing campaign in particular has caught our attention. We have been investigating a trend that has surfaced in recent months involving counterfeit goods messaging spam being sent from North American phone numbers to recipients in China. These messages usually contain references to inexpensive Prada and Coach Handbags as well as other luxury products. Examples of these types of messages include:
��原单正品微信:18302028123
❗奢侈品代工厂原单世界名包��,LV��,普拉达��,香奈儿�� ❗爱马仕,巴宝莉等等,工厂一手货源, ❗每件产品都是高端品。
❗拒绝高仿货,地摊货。 ❗长期招代理支持一件代发, ❗绝对正规广告! ✅原单正品微信:18718881838
✅【支持品牌实体店验货】 绝对正规广告如有打扰,敬请谅解�� 646014B1-9DF3-4C5B-A5A8
Some screenshots of what these scams look like:

From our investigation, and with the help of our carrier partners, we believe that the vast majority of these spam messages have been sent using various models of iPhone, and in particular, by hackers using stolen iCloud account credentials to exploit the ability to send iMessages and SMS remotely.
To recap, this spam campaign has been on-going for several months, but in many cases does not match the standard method of sending SMS abuse in that it is persistent, widely distributed, and the senders are, as far as we could determine, predominately iPhone users that did not exhibit prior spamming behaviour. The timing of when the messages were sent was erratic, but the recurrent nature of the pattern triggered our deeper investigation. We have seen these messages originate from most of the major telecom operators in North America. We have also found reports of many customers noticing that messages to and from China, using both iMessage and SMS, have appeared within their Messages app.
Attack Execution
After much investigation over the past few months, we believe with a high certainty that the attack is actually being executed via compromised iCloud accounts. We believe the steps to reproduce this spam campaign are as follows:
- Hackers obtain compromised iCloud account credentials from various sources (for example: company data breaches, dark web forums, and phishing campaigns).
- The hacker uses the stolen credentials and with them signs onto an Apple device of their own (Mac, iPod, iPhone, iPad, etc.).
- The user who owns the credentials will receive a brief notification on their iPhone that a new device has been paired, like the following. However the notification may be missed by the unsuspecting user, and the notification itself does not have an option to stop access.
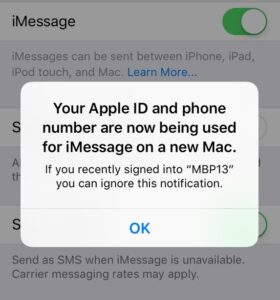
User notification saying that a new mac has signed into the user’s iCloud account
The hacker then sends spam messages to recipients in China using iMessage. If the end recipient in China does not have a data connection at the time (i.e. has iMessage enabled on their iPhone but does not have a data connection through a 3G/4G or WiFi network), the original message is “downgraded” to SMS and sent to the end user. At this point, the message is sent via SMS from the associated user’s device to Chinese handsets.
After much experimentation, we were able to recreate an environment (see below, or here) where the sending iPhone device was remotely controlled and the recipient’s iPhone device was unavailable for iMessage, causing the iMessage to be downgraded down to SMS. There is a sizeable delay before the SMS is sent, but the end result is an effective delivery of spam.
This loss of data connection is common in China as many Chinese users disable their data connection when not used, as data can be relatively expensive for the average user. Some (irate) recipients in China will then respond to the originator iPhone either via iMessage or SMS, leading to the originator thinking that they are getting ‘spammed’.
We have captured a demo of the usage of the Send via SMS feature here, showing how the message gets downgraded to SMS and eventually gets sent:
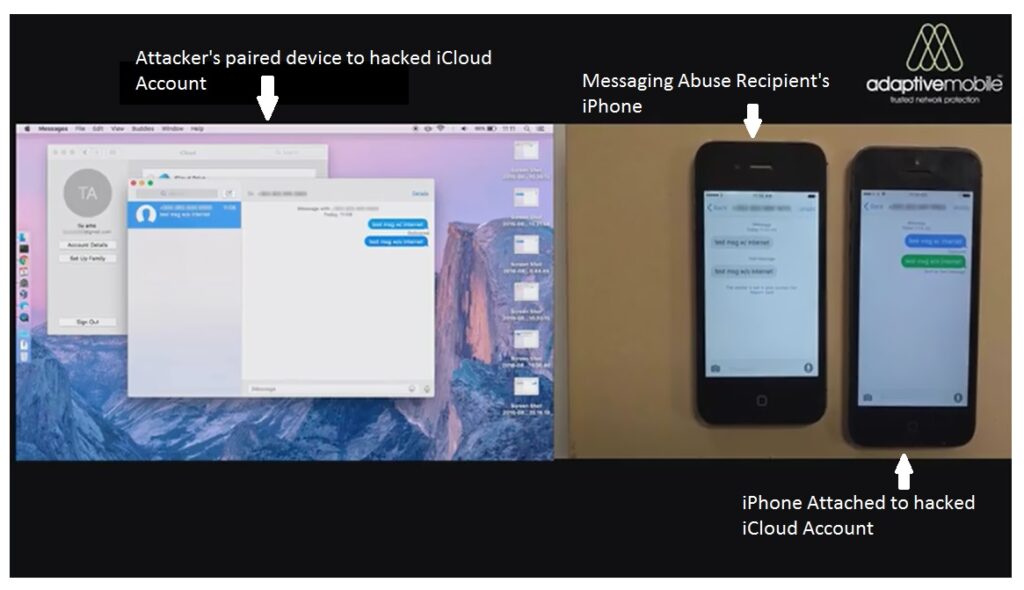
Screenshot from a video on the attack sequence of hacking into a user’s iCloud account
How the Messages are sent from your iPhone
One key question is how exactly the attack is done within the iCloud system. The SMS are being sent using the “Send as SMS” service. This is different from the “Text Message Forwarding” service, which is available through the Continuity feature and is what most people are familiar with. However there are key reasons why the Send as SMS service is used.
The Send as SMS is a fall-back method in case the iMessages can’t be delivered through a data link. After a certain timeout period of unsuccessful attempts, the messages are converted into text messages and sent from an iPhone with this option enabled that is associated with the same account. Text Message Forwarding enables a user to send SMS to anyone from a secondary Apple device linked to your iPhone. The recipient is not limited to iMessage users. The process includes authentication (a PIN is required), which requires somebody to interact with the iPhone sending SMS.
So the key difference is:
- ‘Send as SMS’ is limited to iMessages where both parties have iMessage accounts; for ‘Text Message Forwarding’, the recipient can be anyone.
- ‘Send as SMS’ doesn’t require the spammer to interact with the linked iPhone, while ‘Text Message Forwarding’ requires the hacker to interact with the linked iPhone in order to link up an extra device.
With this distinction, you can see that while Send As SMS is more limited in that the recipient must be an iPhone user, it does not require any Two-Factor-Authentication to be intercepted on a secondary device and thus is a very powerful attack method. Another point is that the attackers probably don’t care if the spam they ‘inject’ into the users’ accounts is sent via iMessage or SMS as long as they are successfully delivered. It is, however, damaging to the user whose account was compromised.
These messages are then sent rapidly in bulk, leading to the account user’s iPhones Messages app conversation list to start showing sent messages which they did not personally send:
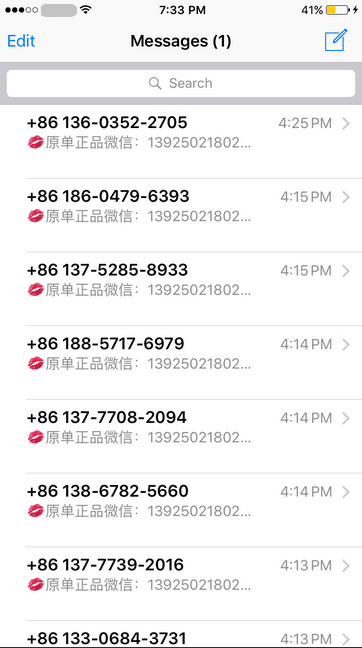
List of sent spam messages on a user’s iPhone after their iCloud account had been hacked into
Overall Impact
Having shown how the iCloud attack can be done, we now can discuss the impact. As well as users having their accounts hacked and being used to send iMessages and SMS, there are also several other consequences. First, the sender is likely to be hit with sizable bills for any large scale number of SMS messages that are being sent to China. Second, they are technically breaking a typical operator’s terms and conditions by sending spam in the first place (with or without their knowledge), and due to this are liable to have their service downgraded or even terminated. Finally, the sender is likely to receive complaints and abuse from those who have received the spam from the compromised iCloud account.
Going into the numbers, we can confirm that the number of affected subscribers is sizable. In the month of July & August, Enea AdaptiveMobile Security detected over 280k SMS messages that matched these patterns being sent from North American carriers to China, from over 3,200 subscriber phone numbers – each one a person who likely had their iCloud account hacked. The sending rates per phone number varied, some of these senders were detected sending thousands of messages leading to a potential sizable bill.
One interesting additional point to note is that North America numbers may be especially attractive to use, as Chinese Mobile Numbers are very similar to North American Numbers. The recipient in China will not easily see a difference on their handset when they receive the message and thus will likely think that the message came from another user in China.
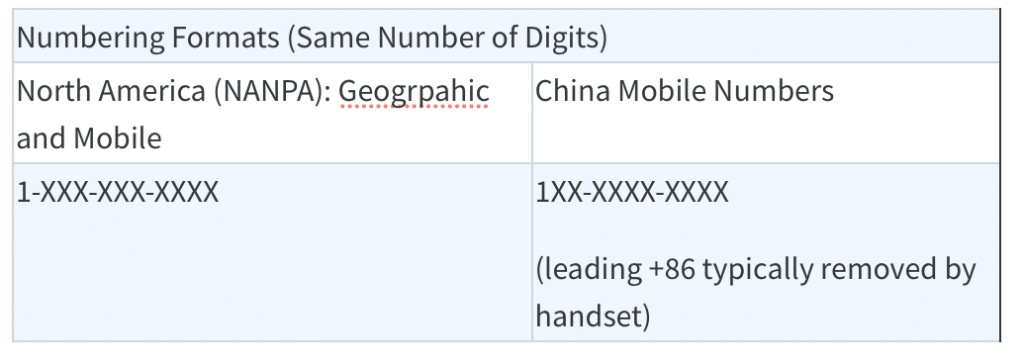
It’s important to remember that iMessages (and domestic) spamming targeting Chinese subscribers has been active for some time. But as we have covered before, there has long been a trend to use international senders, due to the fact that the Chinese operators and the government punish domestic spammers heavily. However, it is much harder for them to deal with spam messages from international SMS sources and from iMessage, making this method much more attractive.
While we have detected and tracked this from North America, there is strong evidence to suggest that other geographies have been infected as well as users in other parts of the world have also reported this.
Stopping the Attack
Discovering how the attack happens is only the first part of the multi-pronged solution that will be needed to stop it. While AdaptiveMobile is capable of blocking the spam when it is converted to SMS, the ultimate fix is via customer education and improvement on iCloud security. In the end, defeating these scammers will take a community effort – not just from Apple, but also from telecom operators and consumers.
Operators can protect their customers from unusual spikes in international traffic, Apple can and do recommend using strong passwords and Two-Factor-Authentication on their accounts, and consumers should learn about and own their own personal security paying particular attention to login alerts from new devices. In the future, Apple should look at ways to further secure iCloud accounts, one potential way would be to ensure that new paired devices are vetted.
In the interim, if you believe that your account has been hacked and is sending messages you don’t recognize, there is some advice online. However, we also recommend performing the steps below:
To deactivate:
1) Go to https://appleid.apple.com, login using your icloud account
2) Change your password:
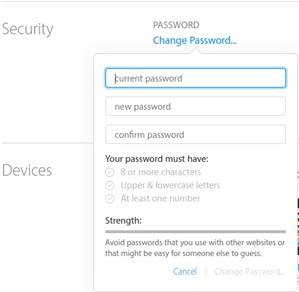
3) Unlink any devices that you don’t recognize:
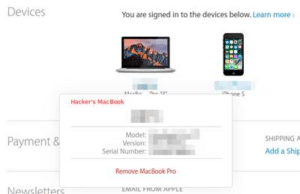
You could also help by never buying a counterfeit handbag, whether that be in Beijing, New York or online!
Many thanks to Yicheng Zhou and Abhijith Pillai for contributing to this blog.